欢迎关注我的公众号:

目前刚开始写一个月,一共写了18篇原创文章,文章目录如下:
istio多集群探秘,部署了50次多集群后我得出的结论
istio多集群链路追踪,附实操视频
istio防故障利器,你知道几个,istio新手不要读,太难!
istio业务权限控制,原来可以这么玩
istio实现非侵入压缩,微服务之间如何实现压缩
不懂envoyfilter也敢说精通istio系列-http-rbac-不要只会用AuthorizationPolicy配置权限
不懂envoyfilter也敢说精通istio系列-02-http-corsFilter-不要只会vs
不懂envoyfilter也敢说精通istio系列-03-http-csrf filter-再也不用再代码里写csrf逻辑了
不懂envoyfilter也敢说精通istio系列http-jwt_authn-不要只会RequestAuthorization
不懂envoyfilter也敢说精通istio系列-05-fault-filter-故障注入不止是vs
不懂envoyfilter也敢说精通istio系列-06-http-match-配置路由不只是vs
不懂envoyfilter也敢说精通istio系列-07-负载均衡配置不止是dr
不懂envoyfilter也敢说精通istio系列-08-连接池和断路器
不懂envoyfilter也敢说精通istio系列-09-http-route filter
不懂envoyfilter也敢说精通istio系列-network filter-redis proxy
不懂envoyfilter也敢说精通istio系列-network filter-HttpConnectionManager
不懂envoyfilter也敢说精通istio系列-ratelimit-istio ratelimit完全手册
————————————————
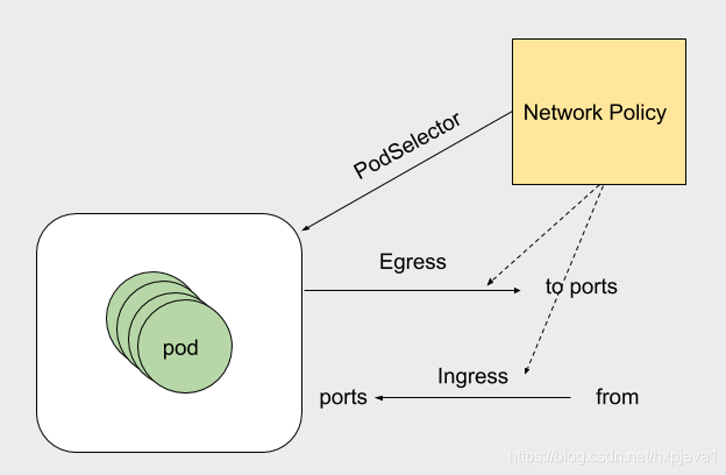
NetworkPolicy:
•使用network policy资源可以配置pod的网络,networkPolicy是namespace scoped的,也就是作用域只是在某个namespace,它只能影响某个namespace下的pod的网络出入站规则。
•不是所有的 Kubernetes 网络方案都支持 Network Policy。比如 Flannel 就不支持
ingress:
deny all:
[root@master01 networkPolicy]# cat default-deny-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny
spec:
podSelector: {}
policyTypes:
- Ingress
allow all:
[root@master01 networkPolicy]# cat allow-all-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all
spec:
podSelector: {}
ingress:
- {}
namespaceSelector:
[root@master01 networkPolicy]# cat namespace-access-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: dev
ports:
- protocol: TCP
port: 80
podSelector:
[root@master01 networkPolicy]# cat podSelector-ingerss.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector:
matchLabels:
app: busybox
ports:
- protocol: TCP
port: 80
ipBlock:
[root@master01 networkPolicy]# cat ip-ingerss.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
namespace: default
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
- Egress
ingress:
- from:
- ipBlock:
cidr: 172.20.59.192/32
整合:
[root@master01 networkPolicy]# cat namespace-podSelector-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: busybox
ports:
- protocol: TCP
port: 80
[root@master01 networkPolicy]# cat namespace-podSelector-ip-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
ingress:
- from:
- ipBlock:
cidr: 172.20.0.0/16
except:
- 172.20.58.195/32
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: busybox
ports:
- protocol: TCP
port: 80
egress:
default deny:
[root@master01 networkPolicy]# cat default-deny-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny
spec:
podSelector: {}
policyTypes:
- Egress
allow all:
[root@master01 networkPolicy]# cat allow-all-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-all
spec:
podSelector: {}
egress:
- {}
policyTypes:
- Egress
namespaceSelector:
[root@master01 networkPolicy]# cat namespace-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: busybox
policyTypes:
- Egress
egress:
- to:
- namespaceSelector:
matchLabels:
project: dev
ports:
- protocol: TCP
port: 80
podSelector:
[root@master01 networkPolicy]# cat podSelector-egerss.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: busybox
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
app: nginx
ports:
- protocol: TCP
port: 80
ipBlock:
[root@master01 networkPolicy]# cat ip-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: busybox
policyTypes:
- Egress
egress:
- to:
- ipBlock:
cidr: 172.20.59.192/32
整合:
[root@master01 networkPolicy]# cat namespace-podSelector-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: busybox
policyTypes:
- Egress
egress:
- to :
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: nginx
ports:
- protocol: TCP
port: 80
[root@master01 networkPolicy]# cat namespace-podSelector-ip-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: busybox
policyTypes:
- Egress
egress:
- to:
- ipBlock:
cidr: 172.20.0.0/16
except:
- 172.20.58.195/32
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: nginx
ports:
- protocol: TCP
port: 80
ingerss egress 完整例子:
[root@master01 networkPolicy]# cat ingress-egress.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: test-network-policy
spec:
podSelector:
matchLabels:
app: nginx
policyTypes:
- Ingress
- Egress
ingress:
- from:
- ipBlock:
cidr: 172.20.0.0/16
except:
- 172.20.58.195/32
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: busybox
ports:
- protocol: TCP
port: 80
egress:
- to:
- ipBlock:
cidr: 172.20.0.0/16
except:
- 172.20.58.195/32
- namespaceSelector:
matchLabels:
project: dev
- podSelector:
matchLabels:
app: nginx
ports:
- protocol: TCP
port: 80










