一.准备环境:
1.centos7 环境
2.安装ansible环境
3.kubernetes安装文件下载路径:
https://dl.k8s.io/v1.24.3/kubernetes-server-linux-amd64.tar.gz
4.kubernetes安装,作者用192.168.126.128,192.168.126.129,192.168.126.130作为kubernetes安装环境,后期可能会有改动
k8s-master | k8s-worker | etcd |
192.168.126.128 | 192.168.126.128 | 192.168.126.128 |
192.168.126.129 | 192.168.126.129 | 192.168.126.129 |
192.168.126.130 | 192.168.126.130 | 192.168.126.130 |
k8s-master节点部署组件 | k8s-worker节点部署组件 | |
kube-apiserver | kubelet | |
kubectl | kube-proxy | |
kube-controller-manager | ||
kube-scheduler |
二.规划:
1.安装变量规划:
kube-apiserver安装路径: apiserver_dir: "/kingdee/kubernetes/kube-apiserver"
kube-apiserver安装IP: apiserver_clusters: "192.168.126.128,192.168.126.129,192.168.126.130"
kube-apiserver端口:apiserver_port: 6443
集群IP计划范围:service-cluster-ip-range:10.96.0.1
etcd服务端地址:etcd-servers: https://192.168.126.128:2379,https://192.168.126.129:2379,https://192.168.126.130:2379
apiserver目录规划:
安装目录:roles/kube-apiserver/{files/ssl,tasks,templates/apiserver,vars}
三.编写 ansible-playbook:
1.创建ansible-playbook剧本目录
mkdir -p roles/kube-apiserver/{files/ssl,tasks,templates/apiserver,vars}
2.创建模板文件:
cd roles/kube-apiserver/templates/apiserver/
#kube-apiserver配置文件:etcd证书为上节所生产 etcd.pem etcd-key.pem
cat > kube-apiserver.conf.j2 <<"EOF"
KUBE_APISERVER_OPTS="--enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction \
--anonymous-auth=false \
--bind-address={{ansible_ssh_host}} \
--secure-port={{apiserver_port}} \
--advertise-address={{ansible_ssh_host}} \
--authorization-mode=Node,RBAC \
--enable-bootstrap-token-auth \
--service-cluster-ip-range={{ip_range}}/16 \
--token-auth-file={{apiserver_dir}}/ssl/token.csv \
--service-node-port-range=30000-32760 \
--tls-cert-file={{apiserver_dir}}/ssl/kube-apiserver.pem \
--tls-private-key-file={{apiserver_dir}}/ssl/kube-apiserver-key.pem \
--client-ca-file={{apiserver_dir}}/ssl/ca.pem \
--kubelet-client-certificate={{apiserver_dir}}/ssl/kube-apiserver.pem \
--kubelet-client-key={{apiserver_dir}}/ssl/kube-apiserver-key.pem \
--service-account-key-file={{apiserver_dir}}/ssl/ca-key.pem \
--service-account-signing-key-file={{apiserver_dir}}/ssl/ca-key.pem \
--service-account-issuer=signing \
--etcd-cafile={{apiserver_dir}}/ssl/ca.pem \
--etcd-certfile={{apiserver_dir}}/ssl/etcd.pem \
--etcd-keyfile={{apiserver_dir}}/ssl/etcd-key.pem \
--etcd-servers={{etcd_servers}} \
--allow-privileged=true \
--apiserver-count=3 \
--audit-log-maxage=30 \
--audit-log-maxbackup=3 \
--audit-log-maxsize=100 \
--audit-log-path={{apiserver_dir}}/logs/kube-apiserver-audit.1og \
--event-ttl=1h \
--alsologtostderr=true \
--logtostderr=false \
--log-dir=/var/log/kubernetes \
--v=4"
EOF#kube-apiserver启动文件
cat > kube-apiserver.service.j2 <<"EOF"
[Unit]
Description= kube-apiserver
Documentation=https://github.com/kubernetes/kubernetes
#After=etcd.service[After etcd starts]
#Wants=etcd.service[After etcd starts]
[Service]
EnvironmentFile=-{{apiserver_dir}}/kube-apiserver.conf
ExecStart=/usr/local/bin/kube-apiserver $KUBE_APISERVER_OPTS
Restart=on-failure
RestartSec=5
Type=notify
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOF3.拿取安装文件及产生相应的证书:
cd roles/kube-apiserver/files/
#拿取etcd安装包
wget https://dl.k8s.io/v1.24.3/kubernetes-server-linux-amd64.tar.gz -O kubernetes-server-linux-amd64.tar.gz
tar -zxvf kubernetes-server-linux-amd64.tar.gzcd roles/kube-apiserver/files/ssl
#配置ca证书请求文件
cat > ca-csr.json <<EOF
{
"CN": "etcd CA",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Beijing",
"ST": "Beijing"
}
]
}
EOF# 创建ca证书
/usr/local/bin/cfssl gencert -initca ca-csr.json|cfssljson -bare ca
注:如果没有cfssl命令则执行一下命令:
wget https://github.com/cloudflare/cfssl/releases/download/v1.6.4/cfssl_1.6.4_linux_amd64
wget https://github.com/cloudflare/cfssl/releases/download/v1.6.4/cfssl-certinfo_1.6.4_linux_amd64
wget https://github.com/cloudflare/cfssl/releases/download/v1.6.4/cfssljson_1.6.4_linux_amd64
chmod +x cfssl*
mv cfssl_1.6.4_linux_amd64 cfssl
mv cfssl-certinfo_1.6.4_linux_amd64 cfssl-certinfo
mv cfssljson_1.6.4_linux_amd64 cfssljson
mv cfssl* /usr/local/bin#配置证书策略
cat > ca-config.json <<"EOF"
{
"signing": {
"default": {
"expiry": "168h"
},
"profiles": {
"kubernetes": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth"
]
},
"client": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
}
}
}
}
EOF#创建kube-apisever证书规则 : host里面为所有apiserver需要用到的IP及域名地址
cat > kube-apiserver-csr.json <<EOF
{
"CN": "kubernetes",
"hosts": [
"192.168.126.128",
"192.168.126.129",
"192.168.126.130",
"127.0.0.1",
"10.96.0.1",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF#创建kube-apisever证书
/usr/local/bin/cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-apiserver-csr.json |cfssljson -bare kube-apiserver#创建token.csv
cat > token.csv <<"EOF"
$(head -c 16 /dev/urandom |od -An -t x|tr -d ' '),kubelet-bootstrap,10001,"system:kubelet-bootstrap"
EOF得到 ca.pem ca-key.pem kube-apiserver-key.pem kube-apiserver.pem
4.编写tasks任务:
cd roles/kube-apiserver/tasks
vim install_apiserver.yml
- name: "mkdir {{apiserver_dir}}"
file:
path: "{{apiserver_dir}}/{{item}}"
state: directory
recurse: true
with_items:
- ssl
- logs
become: yes
- name: "copy ssl to {{apiserver_dir}}/ssl"
copy:
src: "ssl/{{item}}"
dest: "{{apiserver_dir}}/ssl/{{item}}"
with_items:
- ca-key.pem
- ca.pem
- etcd-key.pem
- etcd.pem
- kube-apiserver.pem
- kube-apiserver-key.pem
- token.csv
become: yes
- name: "copy apiserver packge"
copy:
src: kubernetes/server/bin/kube-apiserver
dest: /usr/local/bin/kube-apiserver
mode: 0755
become: yes
- name: "copy apiserver.conf"
template:
src: kube-apiserver.conf.j2
dest: "{{apiserver_dir}}/kube-apiserver.conf"
become: yes
- name: "copy apiserver.service"
template:
src: kube-apiserver.service.j2
dest: /etc/systemd/system/kube-apiserver.service
become: yes
- name: "reload systemctl"
shell: systemctl daemon-reload
become: yes
- name: "start kube-apiserver"
service:
name: kube-apiserver
state: restarted
enabled: true
become: yesvim main.yml
---
- include_tasks: install_apiserver.ymlroles整体目录如下:
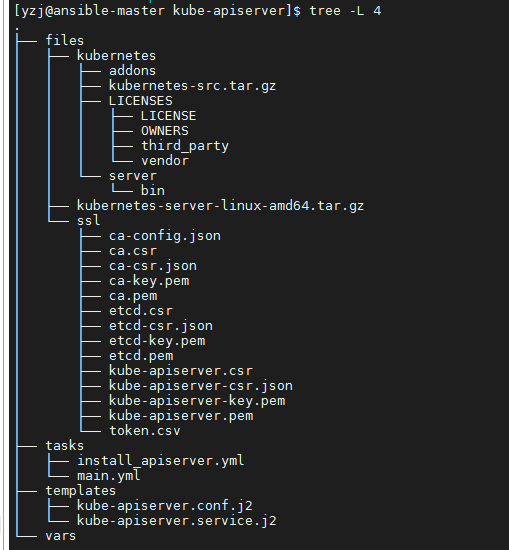
四.编写安装运行文件,和roles处于同级目录
vim startinstall_kube-apiserver.yml
---
- hosts: master
remote_user: yzj
become: no
gather_facts: no
vars:
- apiserver_dir: "/kingdee/kubernetes/kube-apiserver"
- apiserver_cluster: "192.168.126.128,192.168.126.129,192.168.126.130"
- apiserver_port: "6443"
- ip_range: "10.96.0.1"
- etcd_servers: "https://192.168.126.128:2379,https://192.168.126.129:2379,https://192.168.126.130:2379"
roles:
- role: kube-apiserver五.编写hosts,和roles处于同级目录
vim hosts
[master]
k8s-master01 ansible_ssh_host=192.168.126.128
kes-master02 ansible_ssh_host=192.168.126.129
kes-master03 ansible_ssh_host=192.168.126.130六.执行ansiplaybook:
ansible-playbook -i hosts startinstall_kube-apiserver.yml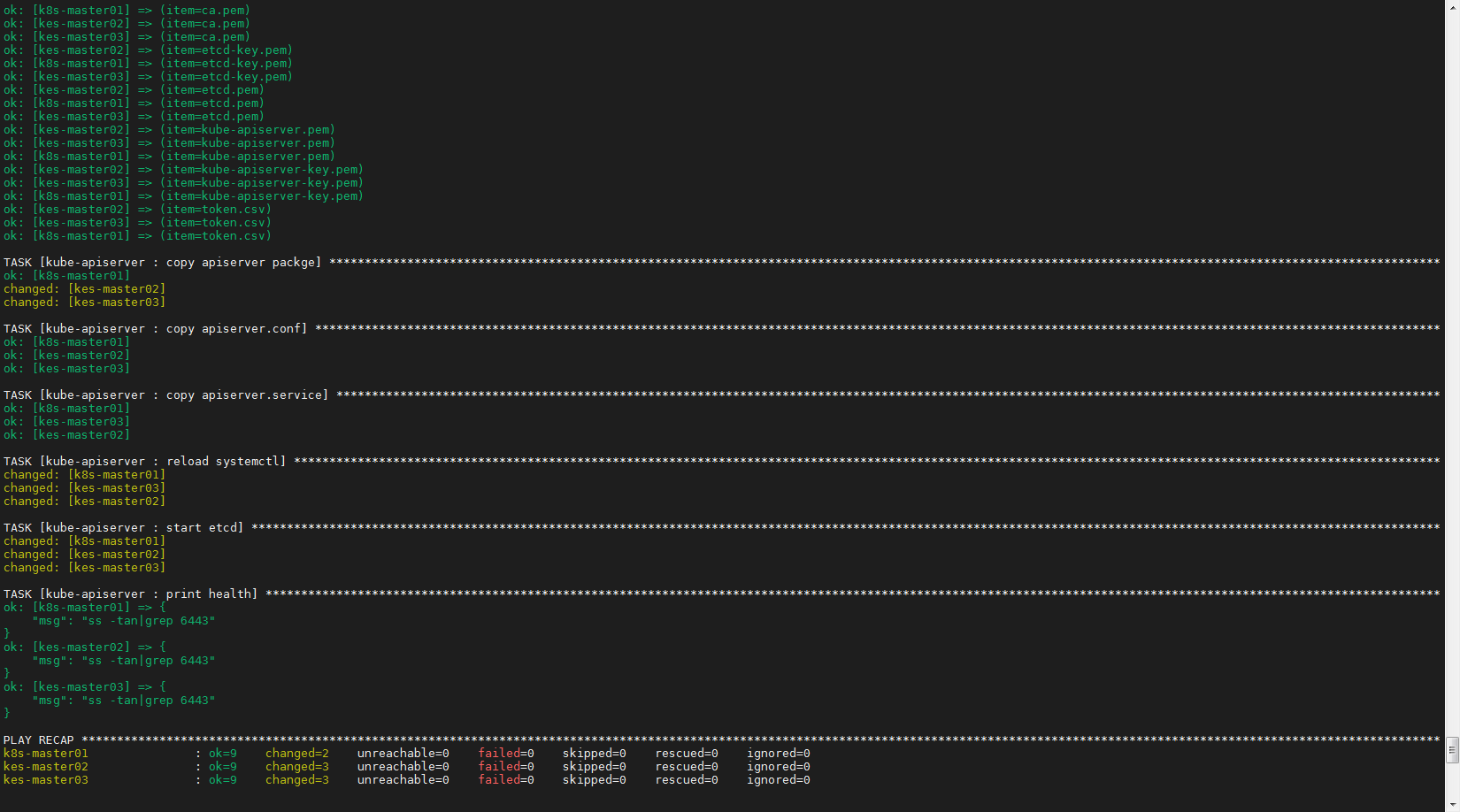
至此,master节点kube-apiserver部署已经介绍完毕,下面就将master节点kubectl部署环节~,敬请期待!










