今日在家详细研究了一下ssh登录的原理,对ssh服务有了很深刻的了解
1.远程命令行管理工具
telnet:明文,不加密,安全性差
ssh:加密,安全连接
openssh
基于PKI:公共密钥体系结构
HTTPS,SSH SSL/TLS
[root@localhost ~]# rpm -qa | grep openssh
openssh-clients-7.4p1-16.el7.x86_64
openssh-7.4p1-16.el7.x86_64
openssh-server-7.4p1-16.el7.x86_64
[root@localhost ~]# whereis ssh
ssh: /usr/bin/ssh /etc/ssh /usr/share/man/man1/ssh.1.gz
[root@localhost ~]# rpm -qf /usr/bin/ssh
openssh-clients-7.4p1-16.el7.x86_64
[root@localhost ~]# rpm -ql openssh-server
/etc/pam.d/sshd
/etc/ssh/sshd_config #服务器端配置文件
/etc/sysconfig/sshd
/usr/lib/systemd/system/sshd-keygen.service
/usr/lib/systemd/system/sshd.service #服务配置文件
/usr/lib/systemd/system/sshd.socket
/usr/lib/systemd/system/sshd@.service
/usr/lib64/fipscheck/sshd.hmac
/usr/libexec/openssh/sftp-server
/usr/sbin/sshd #执行程序
/usr/sbin/sshd-keygen
/usr/share/man/man5/moduli.5.gz
/usr/share/man/man5/sshd_config.5.gz
/usr/share/man/man8/sftp-server.8.gz
/usr/share/man/man8/sshd.8.gz
/var/empty/sshd
[root@localhost ~]# rpm -ql openssh-clients
/etc/ssh/ssh_config #客户端配置文件
/usr/bin/scp
/usr/bin/sftp
/usr/bin/slogin
/usr/bin/ssh
/usr/bin/ssh-add
/usr/bin/ssh-agent
/usr/bin/ssh-copy-id
/usr/bin/ssh-keyscan
/usr/lib64/fipscheck/ssh.hmac
/usr/libexec/openssh/ssh-pkcs11-helper
/usr/share/man/man1/scp.1.gz
/usr/share/man/man1/sftp.1.gz
/usr/share/man/man1/slogin.1.gz
/usr/share/man/man1/ssh-add.1.gz
/usr/share/man/man1/ssh-agent.1.gz
/usr/share/man/man1/ssh-copy-id.1.gz
/usr/share/man/man1/ssh-keyscan.1.gz
/usr/share/man/man1/ssh.1.gz
/usr/share/man/man5/ssh_config.5.gz
/usr/share/man/man8/ssh-pkcs11-helper.8.gz
PKI:
公钥与私钥
1)公钥:加密。保护数据安全,可以公开
2)私钥:解密,可以解密通过公钥加密的数据,成对的那个公钥;用于验证身份,私钥要保护好
公钥与私钥的关系:
1)公钥和私钥是成对出现的
2)唯一性
3)公钥和私钥不能相互推算出来
4)公钥加密,私钥解密 #客户端ssh登录服务器
5)私钥加密,公钥解密 #key身份验证
非对称加密算法 公钥与私钥
1)RSA
[root@localhost ~]# cd /etc/ssh
[root@localhost ssh]# ls
moduli ssh_config sshd_config ssh_host_ecdsa_key ssh_host_ecdsa_key.pub ssh_host_ed25519_key ssh_host_ed25519_key.pub ssh_host_rsa_key ssh_host_rsa_key.pub
[root@localhost ssh]# ls ssh_host_rsa_key*
ssh_host_rsa_key ssh_host_rsa_key.pub
2)ecdsa
3)ed25519
2.SSH远程连接的过程
客户端登录如下:
使用公钥加密,私钥解密
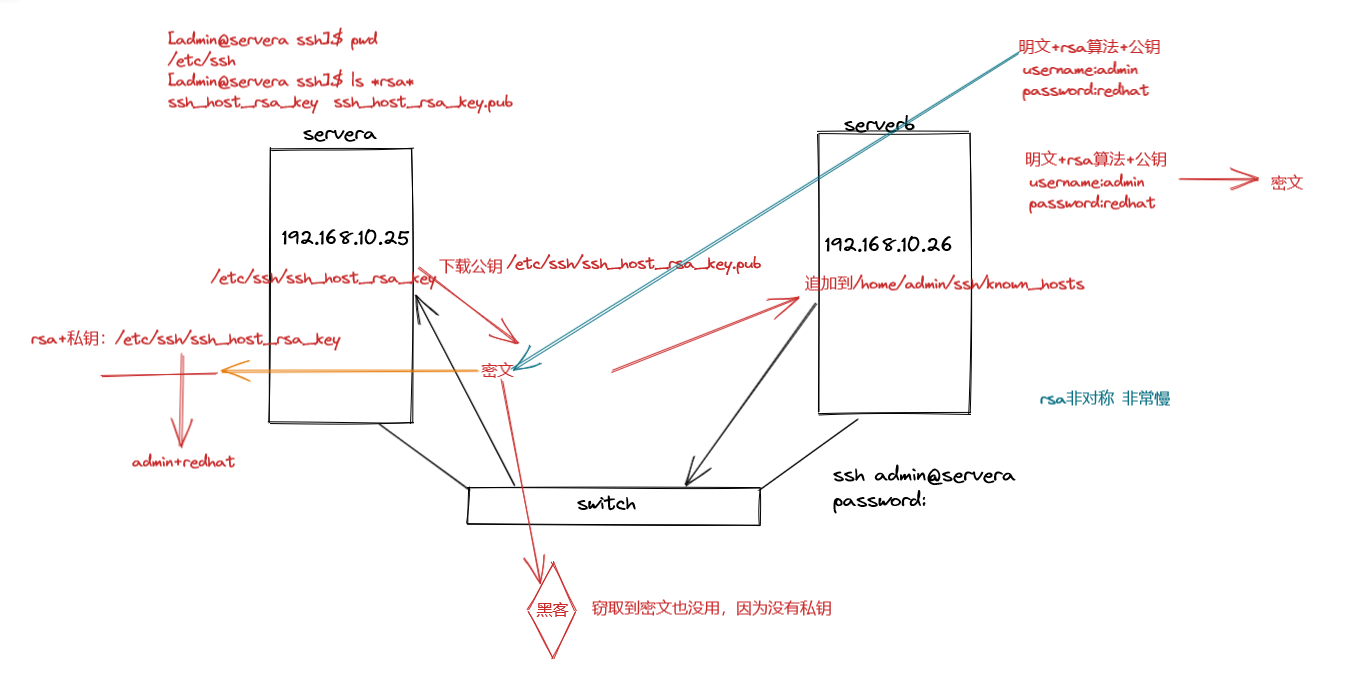
客户端连接过程
当前客户端的公钥 known_hosts文件
[admin@serverb ~]$ ssh admin@192.168.10.25
The authenticity of host '192.168.10.25 (192.168.10.25)' can't be established.
ECDSA key fingerprint is SHA256:ZS4cqrByPcL4hpx1QejC1KjtvXUxprOOGq1dsa6+Wzg.
ECDSA key fingerprint is MD5:e5:a7:4f:f1:bf:f8:01:b2:67:4f:81:42:3e:02:b1:34.
Are you sure you want to continue connecting (yes/no)? no
Host key verification failed.
[admin@serverb ~]$ cd .ssh/
[admin@serverb .ssh]$ ls -al
total 0
drwx------ 2 admin admin 6 Jul 3 15:51 .
drwx------ 6 admin admin 119 Jul 3 15:51 ..
[admin@serverb .ssh]$下载公钥
[admin@serverb .ssh]$ ssh admin@192.168.10.25
The authenticity of host '192.168.10.25 (192.168.10.25)' can't be established.
ECDSA key fingerprint is SHA256:ZS4cqrByPcL4hpx1QejC1KjtvXUxprOOGq1dsa6+Wzg.
ECDSA key fingerprint is MD5:e5:a7:4f:f1:bf:f8:01:b2:67:4f:81:42:3e:02:b1:34.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.10.25' (ECDSA) to the list of known hosts.
admin@192.168.10.25's password:
Last login: Sun Jul 3 15:32:10 2022
[admin@servera ~]$ exit
logout
Connection to 192.168.10.25 closed.
[admin@serverb .ssh]$ ls -al
total 4
drwx------ 2 admin admin 25 Jul 3 15:56 .
drwx------ 6 admin admin 119 Jul 3 15:51 ..
-rw-r--r-- 1 admin admin 175 Jul 3 15:56 known_hosts
[admin@serverb .ssh]$ cat known_hosts
192.168.10.25 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIaJ+CNW9DO+twz14DYh3MhUHZJu4SI8SMb+Vpa058DkomfPuIrZHoiEiKVqzGaoIKCBvqjgFWtybNjcTQTnr70=
[admin@servera ssh]$ cd /etc/ssh
[admin@servera ssh]$ ls
moduli ssh_config sshd_config ssh_host_ecdsa_key ssh_host_ecdsa_key.pub ssh_host_ed25519_key ssh_host_ed25519_key.pub ssh_host_rsa_key ssh_host_rsa_key.pub
[admin@servera ssh]$ cat ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIaJ+CNW9DO+twz14DYh3MhUHZJu4SI8SMb+Vpa058DkomfPuIrZHoiEiKVqzGaoIKCBvqjgFWtybNjcTQTnr70=
后续再次连接就不需要再提示下载公钥了,因为已经下载过了,除非客户端.ssh目录被清空3.使用密钥登录(私钥)
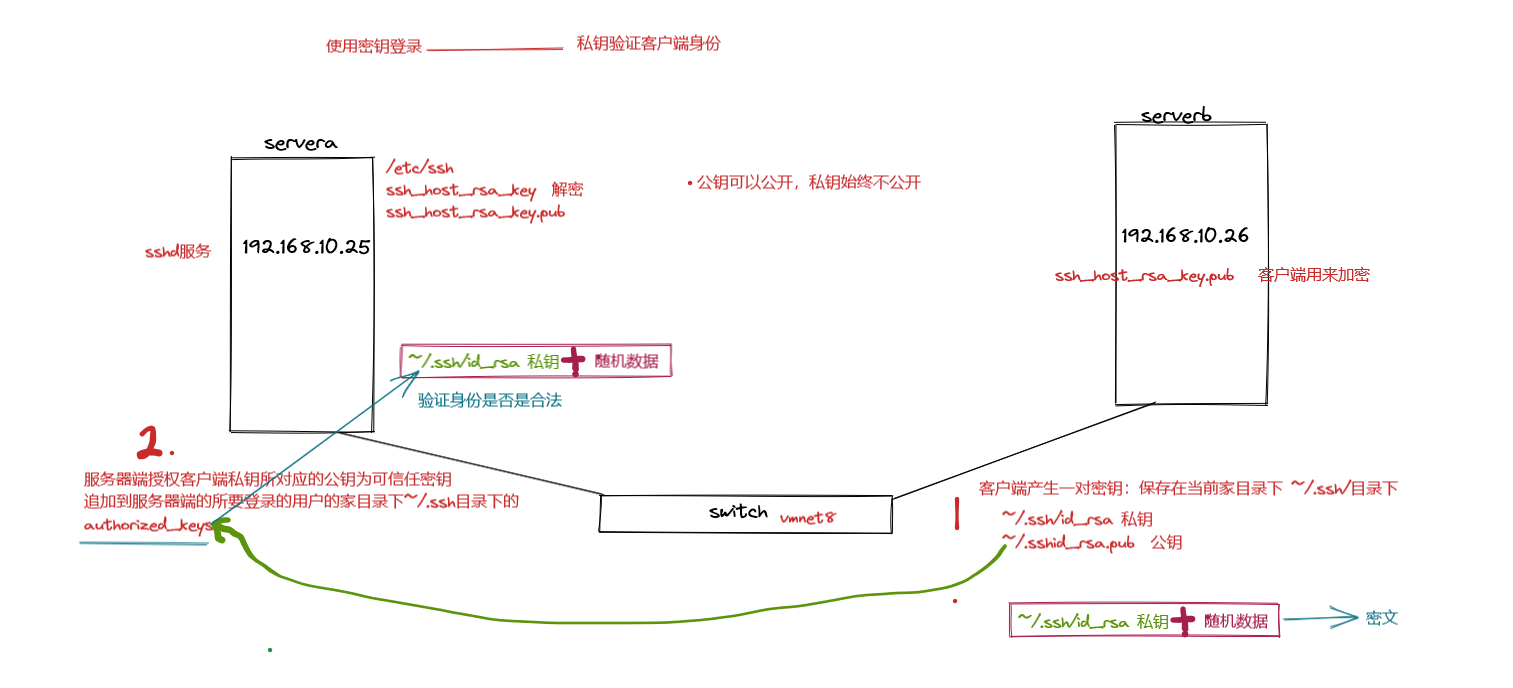
客户端生成密钥
[admin@serverb ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/admin/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/admin/.ssh/id_rsa.
Your public key has been saved in /home/admin/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:3ZeSGtknvM/YvlqXzJDPT5GCbwUC6nyUsK5JypyeaRc admin@serverb
The key's randomart image is:
+---[RSA 2048]----+
| . . |
| + o |
| o o . . |
| + .. =o.o..|
| . +S.+.B+++ |
| o +Eo . o.*O o|
| = o. . .o.*o|
| ..o. .* o.|
| .+. oo*..|
+----[SHA256]-----+
[admin@serverb ~]$ ls /home/admin/.ssh/ -al
total 12
drwx------ 2 admin admin 57 Jul 3 16:11 .
drwx------ 6 admin admin 119 Jul 3 15:51 ..
-rw------- 1 admin admin 1675 Jul 3 16:11 id_rsa
-rw-r--r-- 1 admin admin 395 Jul 3 16:11 id_rsa.pub
-rw-r--r-- 1 admin admin 175 Jul 3 15:56 known_hosts
上传客户端的公钥至服务器端authorized_keys文件中
[admin@servera ~]$ cd ~/.ssh
-bash: cd: /home/admin/.ssh: No such file or directory
[admin@serverb ~]$ ssh-copy-id admin@192.168.10.25
/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/admin/.ssh/id_rsa.pub"
/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
admin@192.168.10.25's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'admin@192.168.10.25'"
and check to make sure that only the key(s) you wanted were added.
[admin@servera ~]$ cd .ssh/
[admin@servera .ssh]$ ls -al
total 4
drwx------ 2 admin admin 29 Jul 3 16:28 .
drwx------ 6 admin admin 140 Jul 3 16:28 ..
-rw------- 1 admin admin 395 Jul 3 16:28 authorized_keys
[admin@servera .ssh]$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDik7M++QzKoAtl9IP8jFnjrFYEAyUfebqqx4DLJIlJxEhE6O1uzgd9veBJxCCt0WsYpDb4stdDYmjgSG9k3zj/GBY0XCPr24RsMyAO9eRar+wbO2hBxxW8ps6v+uWETxSN3TZZDiEjxSLnkOpou0izpui0bFrV8i2WM+ENfMACANi5dvpEmiNLymrCtb31qSj0HYZaZXUnxIaaaP3rZRn/jPoCSxC33VQxHbczjVkxdddWIUnA4aVkmEMUEuHNjL4I/i6Qv0Ua/vxlM8ZMzP2YrsUjLwgMOYI+bojlfqHdIhG09KpCtOcmt8nZnawLTd5wluJWHf4kTeFDjRVp+XSB admin@serverb
[admin@serverb ~]$ cd .ssh/
[admin@serverb .ssh]$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDik7M++QzKoAtl9IP8jFnjrFYEAyUfebqqx4DLJIlJxEhE6O1uzgd9veBJxCCt0WsYpDb4stdDYmjgSG9k3zj/GBY0XCPr24RsMyAO9eRar+wbO2hBxxW8ps6v+uWETxSN3TZZDiEjxSLnkOpou0izpui0bFrV8i2WM+ENfMACANi5dvpEmiNLymrCtb31qSj0HYZaZXUnxIaaaP3rZRn/jPoCSxC33VQxHbczjVkxdddWIUnA4aVkmEMUEuHNjL4I/i6Qv0Ua/vxlM8ZMzP2YrsUjLwgMOYI+bojlfqHdIhG09KpCtOcmt8nZnawLTd5wluJWHf4kTeFDjRVp+XSB admin@serverb
使用密钥验证身份:默认~/.ssh/id_rsa
指定密钥位置
[admin@serverb .ssh]$ ls
id_rsa id_rsa.pub known_hosts
[admin@serverb .ssh]$ cp id_rsa serverb_key
[admin@serverb .ssh]$ ssh -i serverb_key admin@192.168.10.25
Last login: Sun Jul 3 15:56:17 2022 from 192.168.10.26
注:不指定则默认使用id_rsa
[admin@servera ~]$








